“We were getting alerts, but by the time we reviewed logs on each server, the attack was over.”
— Senior SOC Analyst at a mid-sized Indian bank (client anonymized)
In early 2024, one of our consulting clients — a mid-sized financial services provider in Mumbai — faced a serious cyber threat. A credential stuffing attack targeted staff accounts. While antivirus software eventually flagged the activity, the delay in manually reviewing logs across 63 different Windows endpoints allowed lateral movement to go undetected.
Table of Contents
🚨 The Real Problem
Despite existing tools, their IT team relied on RDP and local Event Viewer for forensic analysis. No SIEM was fully in place, and logs were dispersed. Their internal SLA to triage incidents was 4 hours — too slow for modern threats.
✅ The Solution: Windows Event Log Subscriptions (WEF)
Over a 5-day rollout, we:
- Deployed WEF using source-initiated subscriptions
- Used HTTPS with certificate authentication over WinRM (5986)
- Filtered logs at the source using custom XML queries
- Integrated the collector with Microsoft Sentinel via Winlogbeat
📈 Results After 2 Months
- 🚀 Reduced incident response time from 3 hours → 30 minutes
- 💰 Cut log ingestion volume by 28% before reaching SIEM
- 📋 Passed internal RBI audit a full month early
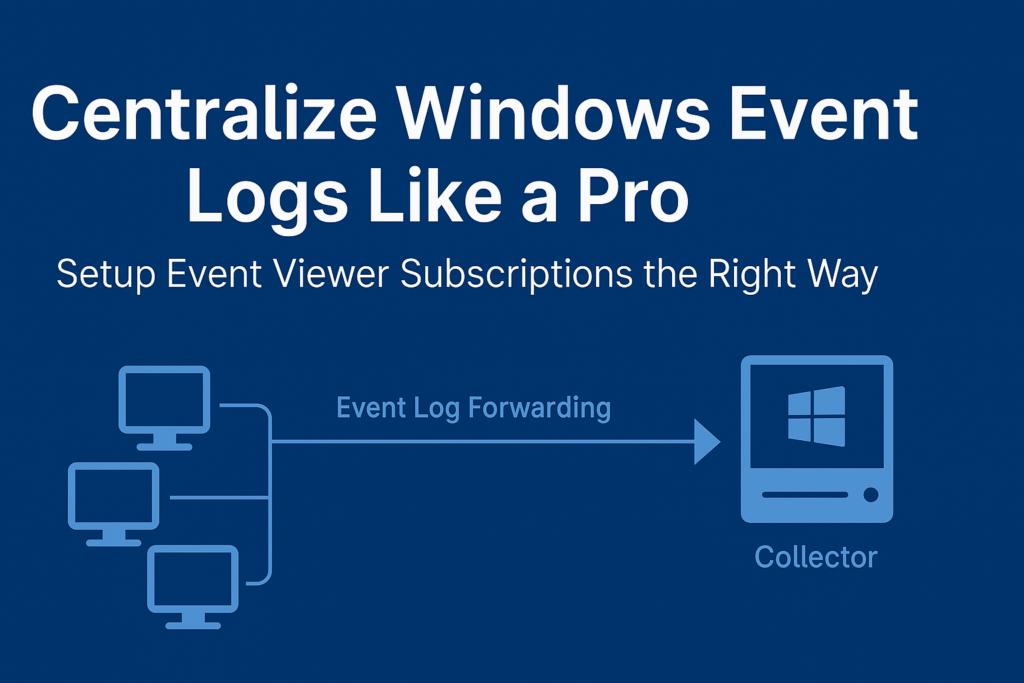
🧠 What Are Windows Event Log Subscriptions?
Windows Event Log Subscriptions allow centralized collection of logs using native tools in Windows. A central collector server receives logs from other systems in your domain, using Windows Event Forwarding (WEF).
Key technologies:
- WinRM (Windows Remote Management) for log transport
- Group Policy to enroll endpoints
- Event Viewer Subscriptions to configure filters
Architecture Overview
+------------------+ HTTPS (5986) +-------------------+
| Workstation A | --------------------> | Collector Server |
| Domain Member | --------------------> | (Event Viewer + SIEM) |
+------------------+ +-------------------+
Two types of subscriptions:
- Source-Initiated Subscription: In this model, the client systems (also known as event sources) proactively send their logs to the collector server. It’s the preferred method for enterprise environments because it’s easier to scale and manage. Clients are configured through Group Policy to register themselves with the collector, which reduces the need for centralized configuration or discovery. This model supports dynamic environments where machines may be added or removed frequently.
- Collector-Initiated Subscription: Here, the collector server initiates the connection and requests logs from each client machine. While this method gives the collector more control, it is more cumbersome to manage at scale. It requires the collector to maintain an up-to-date list of all source computers and establish individual connections, which becomes problematic in large, distributed networks. This method is more suitable for small, static environments or when network constraints prevent source-initiated connections.
🎯 Why Should You Care?
| Challenge | WEF Solution |
|---|---|
| Distributed logs | Centralized console (Event Viewer) |
| Missed alerts | Real-time forwarding to SIEM |
| Audit pressure | Central record of user/system behavior |
| High SIEM cost | Pre-filter logs at source (save GBs/month) |
🛠️ Implementation Guide
✅ Step 1: Prep the Collector
- Use Windows Server 2019/2022 (or Win10/11 Pro for testing)
- Enable WinRM:
winrm quickconfig - Start Windows Event Collector service:
services.msc → Windows Event Collector → Automatic → Start
✅ Step 2: Create Secure Subscription
- Open Event Viewer > Subscriptions > Create Subscription
- Choose Source-Initiated
- Apply XML Filter:
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=4625 or EventID=4624 or EventID=4688)]]
</Select>
</Query>
</QueryList>
- Save and exit
✅ Step 3: Configure Source Machines via GPO
In Group Policy Management Console:
- Enable WinRM:
Computer Configuration > Policies > Admin Templates > Windows Components > WinRM - Set Subscription Manager:
Computer Configuration > Admin Templates > Event Forwarding > Configure Target Subscription ManagerExample:Server=https://collector.bank.local:5986/wsman/SubscriptionManager/WEC,Refresh=60 - Apply GPO to OU
- Run
gpupdate /forceon clients
✅ Step 4: Verify & Monitor
- Open
Event Viewer > Forwarded Eventson the collector - Validate log delivery from each endpoint
🔐 Security Hardening (Critical for Trust)
| Practice | Why It Matters |
|---|---|
| Use HTTPS (WinRM over 5986) | Encrypt log transport |
| Cert-based auth | Prevent spoofed log sources |
| Access control on Event Viewer | Limit log visibility to SOC team only |
| Enable WEC auditing | Monitor for forwarding failures |
📈 Integration with SIEM (e.g., Microsoft Sentinel)
You can forward logs from the WEF collector using:
- Winlogbeat (Elastic Stack)
- NXLog (for complex pipelines)
- Azure Log Analytics agent
Real Tip: Pre-filter logs via XML to drastically reduce ingestion volume and licensing cost.
📚 References
- Microsoft: Windows Event Forwarding Overview
- Event ID Encyclopedia: Ultimate Windows Security
🧾 Final Takeaway
Don’t wait for a breach to fix your logging strategy. Windows Event Log Subscriptions give you free, scalable, and secure visibility into your IT environment. All it takes is proper planning, filtering, and execution.
“You can’t protect what you can’t see — start centralizing logs today.”